Table of Contents
The cash money conversion cycle (CCC) is one of numerous measures of monitoring efficiency. It determines just how fast a business can convert cash money on hand into also more money handy. The CCC does this by adhering to the money, or the resources investment, as it is first converted right into stock and accounts payable (AP), with sales and receivables (AR), and afterwards back right into cash money.

A is the use of a zero-day manipulate to create damage to or take information from a system influenced by a susceptability. Software application usually has safety and security vulnerabilities that cyberpunks can manipulate to trigger mayhem. Software application programmers are constantly watching out for susceptabilities to "spot" that is, create an option that they launch in a new update.
While the vulnerability is still open, opponents can write and carry out a code to benefit from it. This is referred to as manipulate code. The manipulate code might bring about the software application individuals being preyed on as an example, with identification burglary or other kinds of cybercrime. When attackers recognize a zero-day vulnerability, they need a method of getting to the at risk system.
The Basic Principles Of Security Consultants
Protection susceptabilities are commonly not found directly away. In current years, cyberpunks have actually been much faster at manipulating susceptabilities quickly after discovery.
: cyberpunks whose inspiration is generally monetary gain cyberpunks encouraged by a political or social cause that desire the attacks to be visible to attract interest to their reason hackers who snoop on business to obtain information concerning them countries or political stars snooping on or assaulting another nation's cyberinfrastructure A zero-day hack can make use of susceptabilities in a selection of systems, including: As an outcome, there is a wide variety of possible targets: Individuals who make use of an at risk system, such as a web browser or running system Hackers can utilize protection susceptabilities to jeopardize gadgets and build large botnets Individuals with access to important service data, such as intellectual building Hardware gadgets, firmware, and the Internet of Points Large companies and companies Federal government agencies Political targets and/or nationwide protection threats It's practical to assume in terms of targeted versus non-targeted zero-day strikes: Targeted zero-day assaults are accomplished against possibly valuable targets such as large companies, federal government companies, or high-profile people.
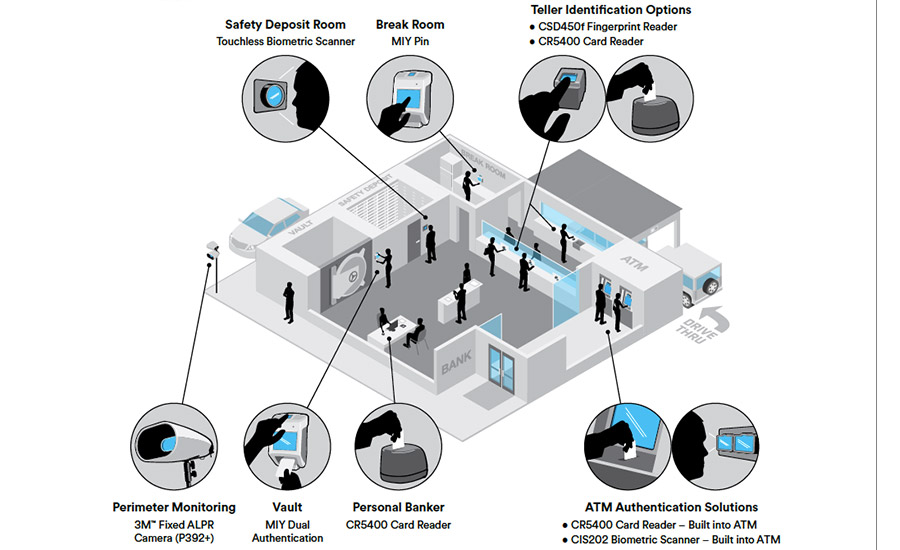
This site uses cookies to assist personalise material, customize your experience and to keep you visited if you sign up. By continuing to utilize this site, you are consenting to our use cookies.
The Main Principles Of Banking Security
Sixty days later on is generally when an evidence of principle emerges and by 120 days later on, the vulnerability will certainly be included in automated susceptability and exploitation tools.
Before that, I was simply a UNIX admin. I was believing concerning this concern a lot, and what struck me is that I do not know as well numerous individuals in infosec that chose infosec as a career. Most of the people that I know in this field really did not most likely to college to be infosec pros, it simply kind of happened.
Are they interested in network safety and security or application security? You can get by in IDS and firewall world and system patching without recognizing any kind of code; it's relatively automated things from the product side.
The Banking Security PDFs
With gear, it's much various from the job you do with software program safety. Would certainly you state hands-on experience is more important that official protection education and accreditations?
There are some, however we're possibly talking in the hundreds. I think the universities are simply currently within the last 3-5 years getting masters in computer system safety and security sciences off the ground. There are not a great deal of pupils in them. What do you think is the most essential certification to be effective in the safety space, regardless of a person's background and experience level? The ones that can code often [fare] much better.
And if you can recognize code, you have a better possibility of being able to recognize just how to scale your solution. On the protection side, we're out-manned and outgunned frequently. It's "us" versus "them," and I don't recognize the amount of of "them," there are, however there's going to be as well few of "us "at all times.
The Ultimate Guide To Banking Security
For example, you can think of Facebook, I'm not exactly sure many security individuals they have, butit's mosting likely to be a small portion of a percent of their user base, so they're mosting likely to need to find out just how to scale their options so they can protect all those individuals.
The researchers observed that without recognizing a card number beforehand, an enemy can launch a Boolean-based SQL injection via this area. The database reacted with a 5 2nd hold-up when Boolean true statements (such as' or '1'='1) were offered, resulting in a time-based SQL shot vector. An assaulter can use this trick to brute-force query the data source, permitting info from easily accessible tables to be revealed.
While the information on this dental implant are scarce presently, Odd, Work functions on Windows Web server 2003 Enterprise approximately Windows XP Specialist. Several of the Windows exploits were also undetected on online file scanning solution Virus, Total amount, Safety Designer Kevin Beaumont validated through Twitter, which shows that the devices have not been seen prior to.
Navigation
Latest Posts
Diy Plumbing close to Boston, Massachusetts
Diy Plumbing near me Boston
Should I Plumb My Own Home around me Boston